
Azure Logic App Tricks Part-1
September 9, 2025
azureintegrationlogic-appsIntroduction
TL;DR — Short, practical tips to make Azure Logic Apps more robust and production-ready. This post covers schema validation, JSON parsing shortcuts, authentication setup, and trigger concurrency control.
In this article I focus on Azure Logic Apps tips that I used in real projects and want to share with integration engineers accross the community.
Azure Logic Apps
1. Schema validation
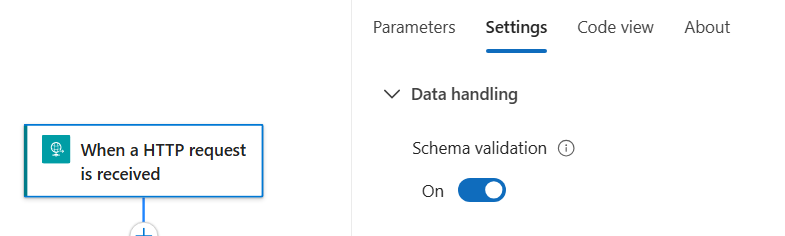
- For HTTP triggers, enable schema validation so the workflow triggers only when the incoming payload matches the expected shape. This keeps run history clean and makes failures easier to diagnose.
- Schema validation is only available on HTTP triggers (UI setting). Use it when you control the caller or can define a stable contract.
- For Parse JSON: you can define field length, required fields, and enums. Example JSON Schema to enforce a max length:
{
"type": "object",
"properties": {
"invNo": {
"type": "string",
"maxLength": 20
}
},
"required": ["invNo"]
}
Refer to the official JSON Schema docs here.
2. JSON parsing
Instead of always using the Parse JSON action (which requires a strict schema and can break on changes), use expressions to access nested fields safely.
Example payload:
{
"order": {
"order_id": "ORD-0000001221",
"qty": 1.01,
"amount": 10024,
"currency_code": "INR",
"unit": "pcs"
}
}
Access a field using an expression:
triggerBody()?['order']?['order_id']
Or in code view string formatting:
@"{triggerBody()?['order']?['order_id']}
Use this approach for resilience when producers may change the payload shape.
3. Authentication (OAuth2)
For OAuth2, set up the authorization on the action and create a policy where needed.
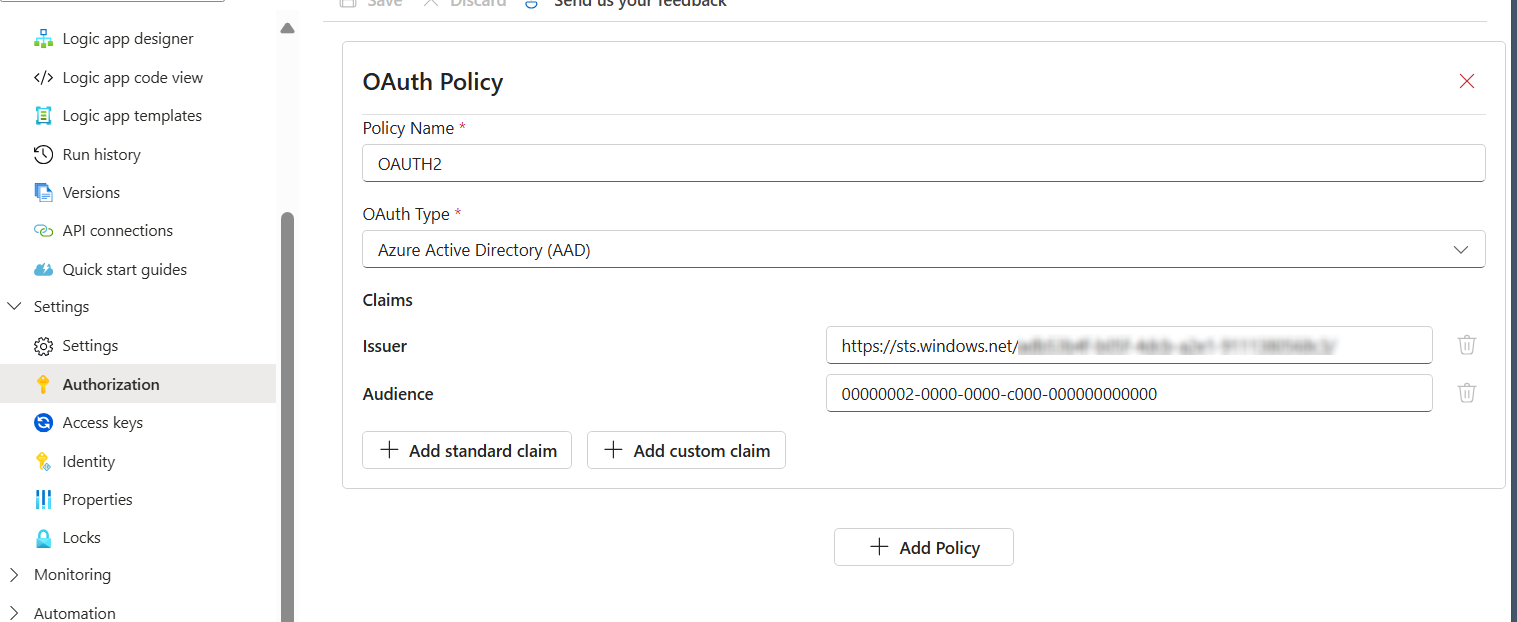
Common values that work for MS Entra / AAD setups:
iss: https://sts.windows.net/<tenant-id>
aud: 00000002-0000-0000-c000-000000000000
For token generation, set audience appropriately:
aud: https://sts.windows.net/<tenant-id>
To decode tokens for troubleshooting use jwt.ms.
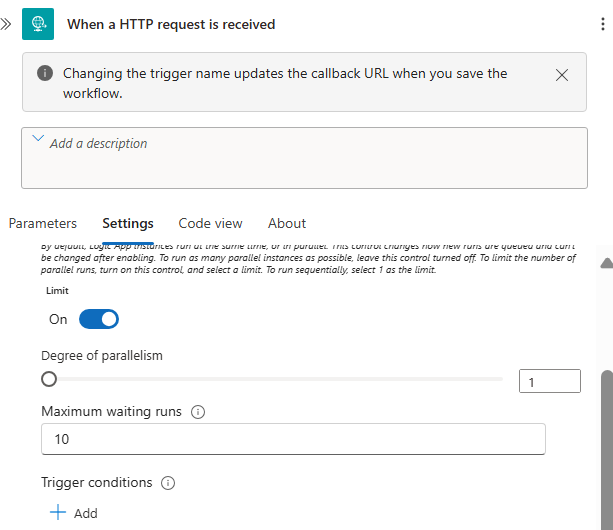
4. Trigger concurrency control
If your downstream systems cannot handle parallel requests (e.g. ERP tables with locks), control concurrency on the trigger.
- Set concurrency to 1 when you need strict ordering or to avoid locking conflicts.
- Adjust the maximum queued requests and wait behavior to avoid runaway timeouts.
5. Authentication on HTTP actions
When calling OAuth2-protected endpoints, you can configure token generation inside the HTTP action so every request gets a fresh token without manual token management.
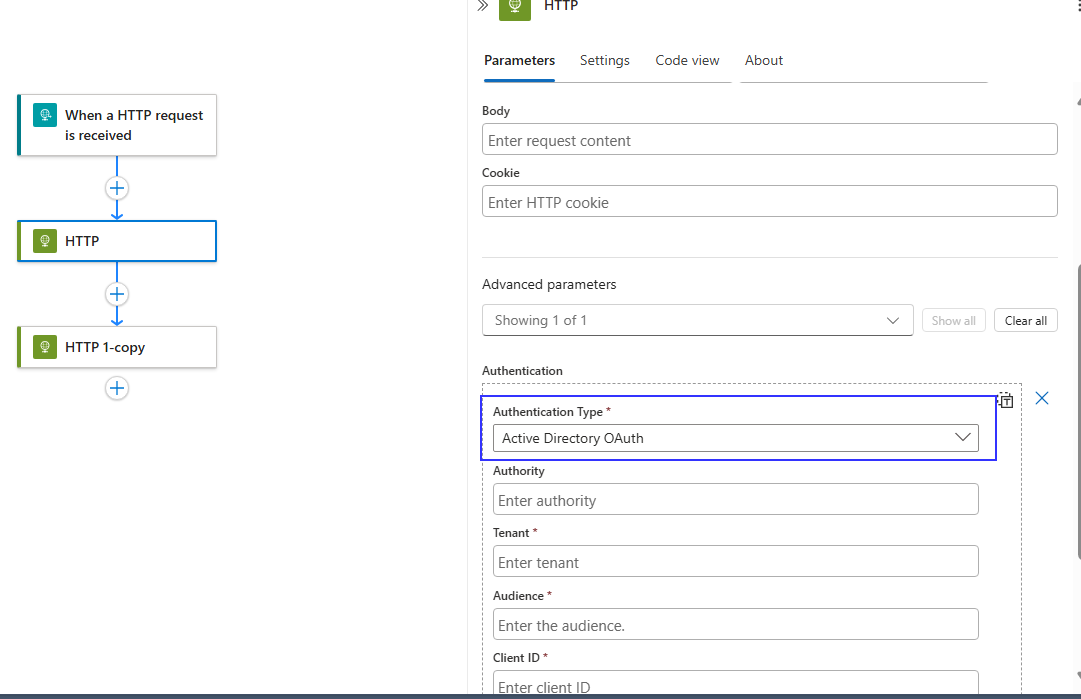
Tip: Match the audience claim to the resource for correct token validation.
Key takeaways
- Use schema validation for contractual controls.
- Prefer expression-based access for flexible parsing.
- Harden auth and prefer built-in token management where possible.
- Use trigger concurrency to protect downstream systems.
If you found this useful, please share it to help other integration engineers.
Thanks for reading, Keep learning keep growing.
Reach out me contact information