
Azure Endpoints - Decision Factors
October 10, 2025
azuresecurityendpointsSecuring Azure Services: Service Endpoints vs Private Endpoints
Security usually comes after we get the service running. And by “after,” I mean once it's already in production, users are on it, and suddenly someone asks:
“Wait… is this actually secure?”
At that point, you either scramble for documentation or—if you’re unlucky—your friendly neighborhood hacker finds out before you do. Let’s avoid that.
In this post, I'll walk you through Service Endpoints vs Private Endpoints, what they are, how they differ, and when you should care. I even set up a small experiment in my lab (a.k.a. one tired subscription in Central India) to see this in action.
My Lab Setup
Here’s what I wired up:
- VNet in Central India
- Two subnets
- default subnet: has NICs for VMs
- storageaccount subnet: private-only, no internet connectivity
- Two Storage Accounts (with static website enabled):
stgstaticblob→ connected via Private Endpointstgstaticblobv2→ connected via Service Endpoint
- Website content: one lonely file,
error.html(because my design skills peaked there).
This setup gave me a chance to compare both approaches in real-world scenarios. Here's what I found:
1. Service Endpoints
Think of Service Endpoints as giving your subnet a VIP pass to talk directly to certain Azure services.
- Pros
- No extra cost
- Easy setup you just tell Azure: “This subnet can talk to that service.”
- Cons
- Limited coverage only works with a defined list of Azure services.
- Doesn’t play well with VPN Gateways. Works with ExpressRoute, but… with conditions.
In short: great for keeping traffic inside Azure's backbone network, but not a full-on “private” solution.
👉 Read more about Service Endpoints here.
2. Private Endpoints
Now, Private Endpoints are a different beast. They give you a truly private connection by assigning a NIC with a private IP from your subnet to the Azure service.
- Pros
- Really private no exposure to public internet at all.
- Works with most Azure services (not just a select list).
- On-premises friendly your on-prem infrastructure can also use it (via VPN/ExpressRoute).
- Cons
- Costs money billed per hour + per GB of traffic.
- Requires Private DNS Zones for name resolution.
👉 Read more about Private Links here.
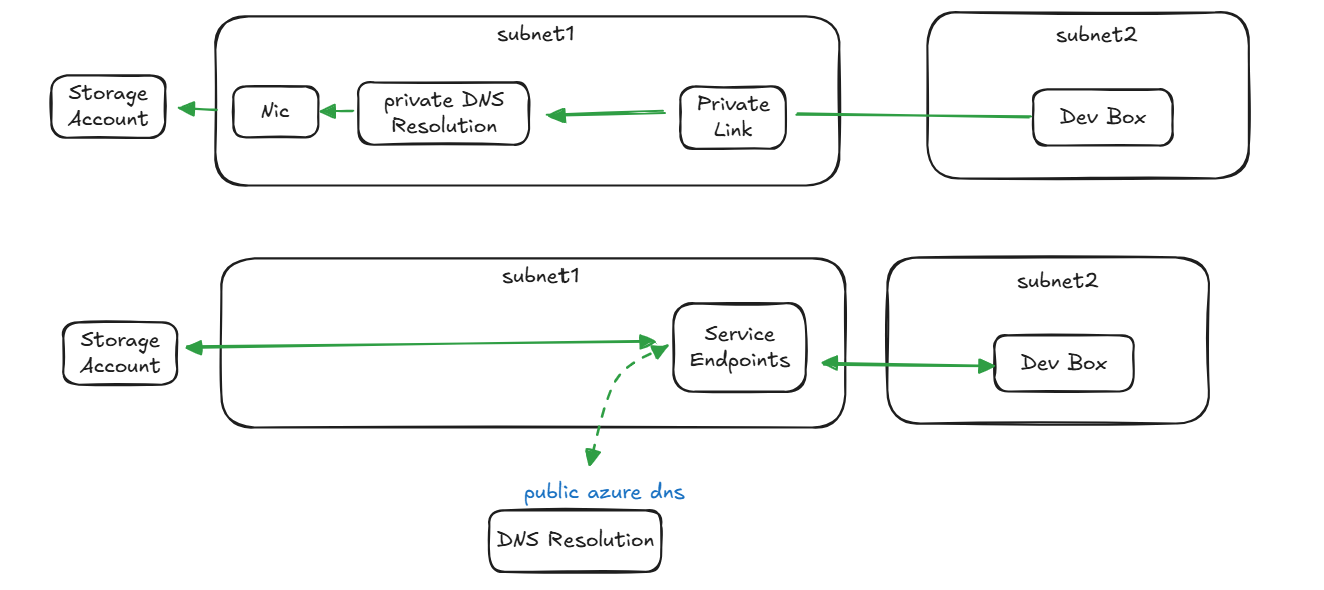
Service Endpoint vs Private Endpoint
Here's the subtle but important difference:
- With Service Endpoints, your storage account can still be reachable from public internet unless you explicitly disable public access. The “restriction” is more about who inside your VNet can access it.
- With Private Endpoints, the service literally lives inside your VNet with a private IP. DNS points your requests to that private NIC. Public internet doesn’t even know it exists.
So the real decision factor is:
- Do you just want Azure backbone isolation at no cost? → Go Service Endpoint.
- Do you need total secrecy, on-prem integration, and no internet exposure? → Go Private Endpoint.
Here's a visual (because words are boring without diagrams):
Final Thoughts
Service Endpoints are like backstage passes: you skip the public crowd and go directly inside, but the event is still happening in a public stadium.
Private Endpoints are like a private house party: if you’re not on the list and inside the house, you don’t even know the party exists.
Both have their uses it's just about picking the right tool for the right scenario.
Thanks for reading! Keep learning, keep growing.
You can always reach me here.